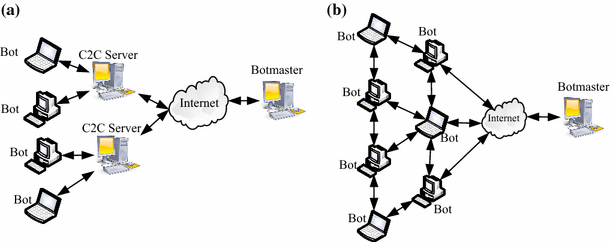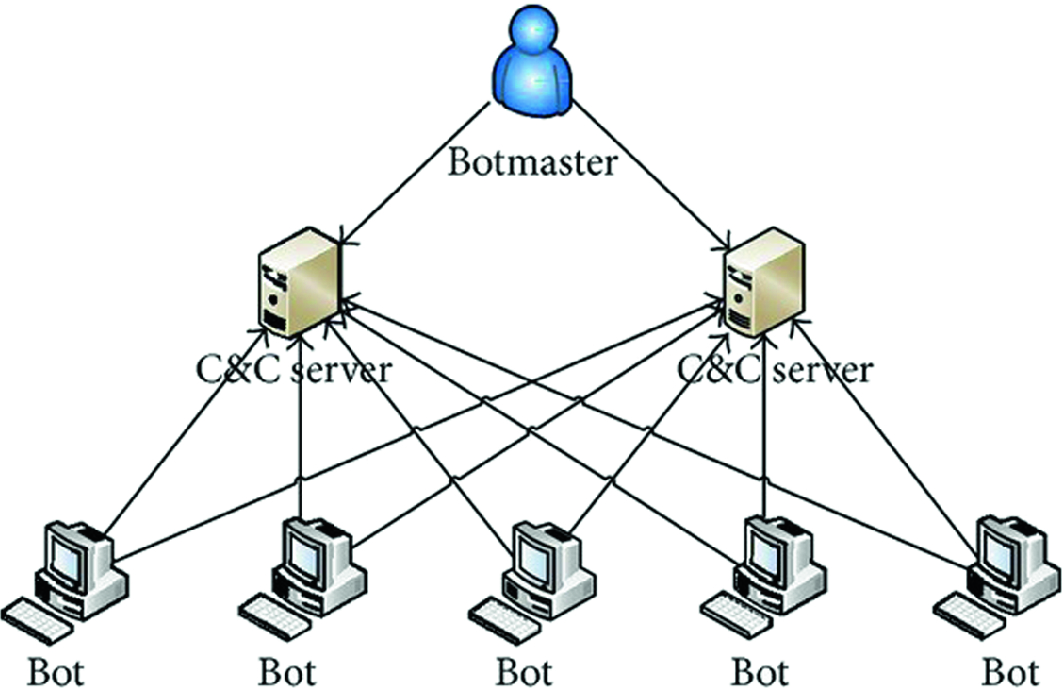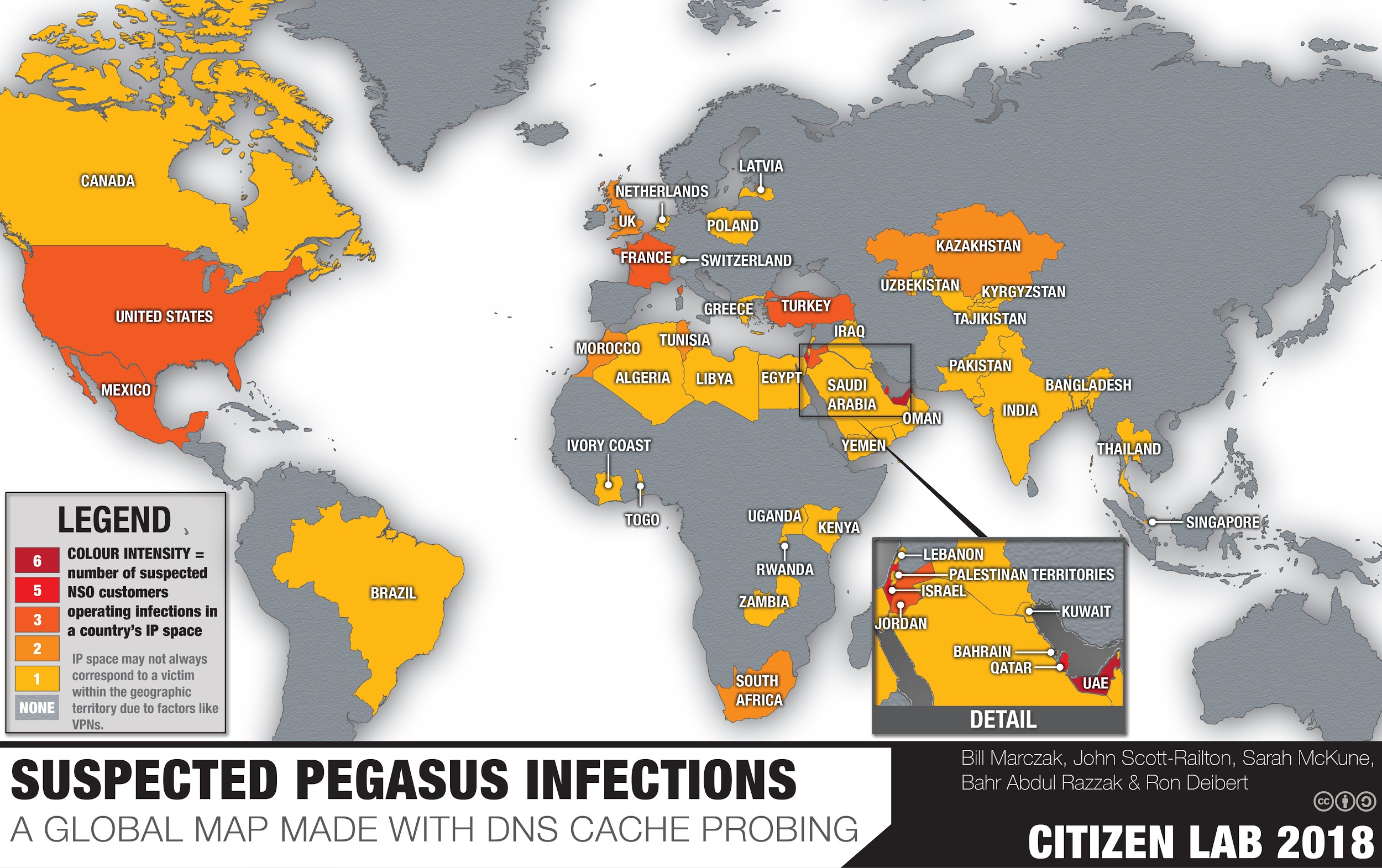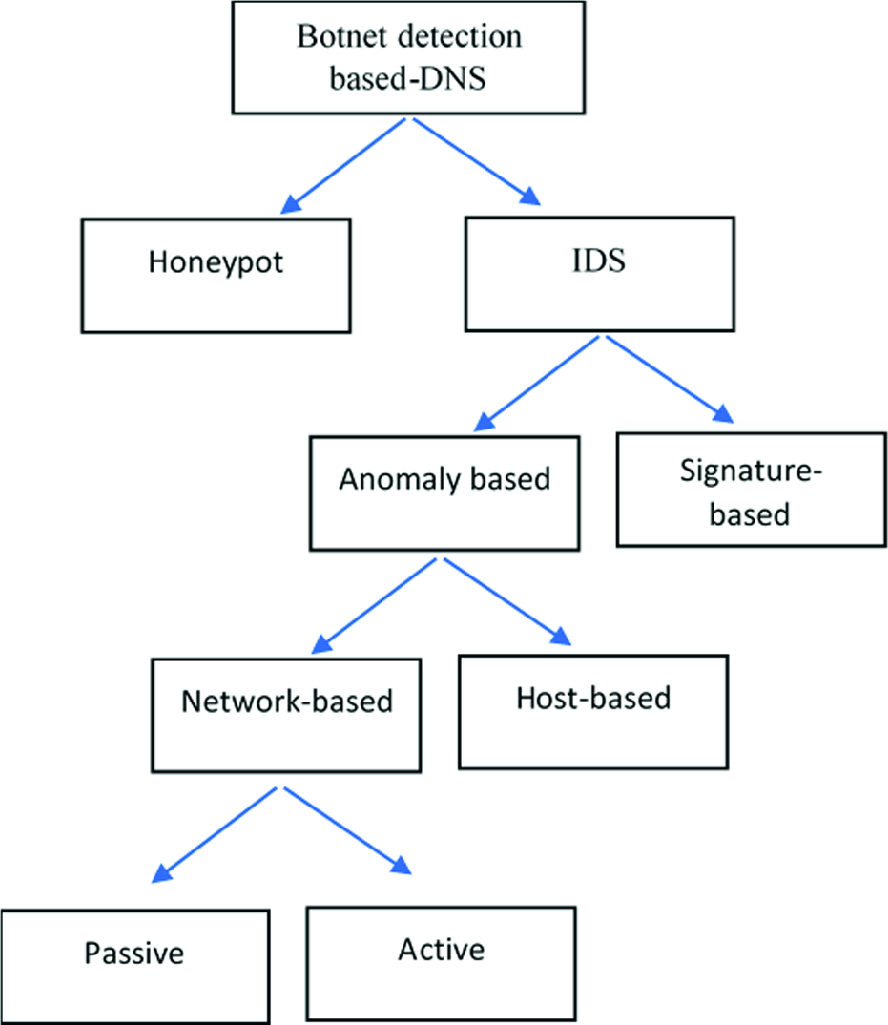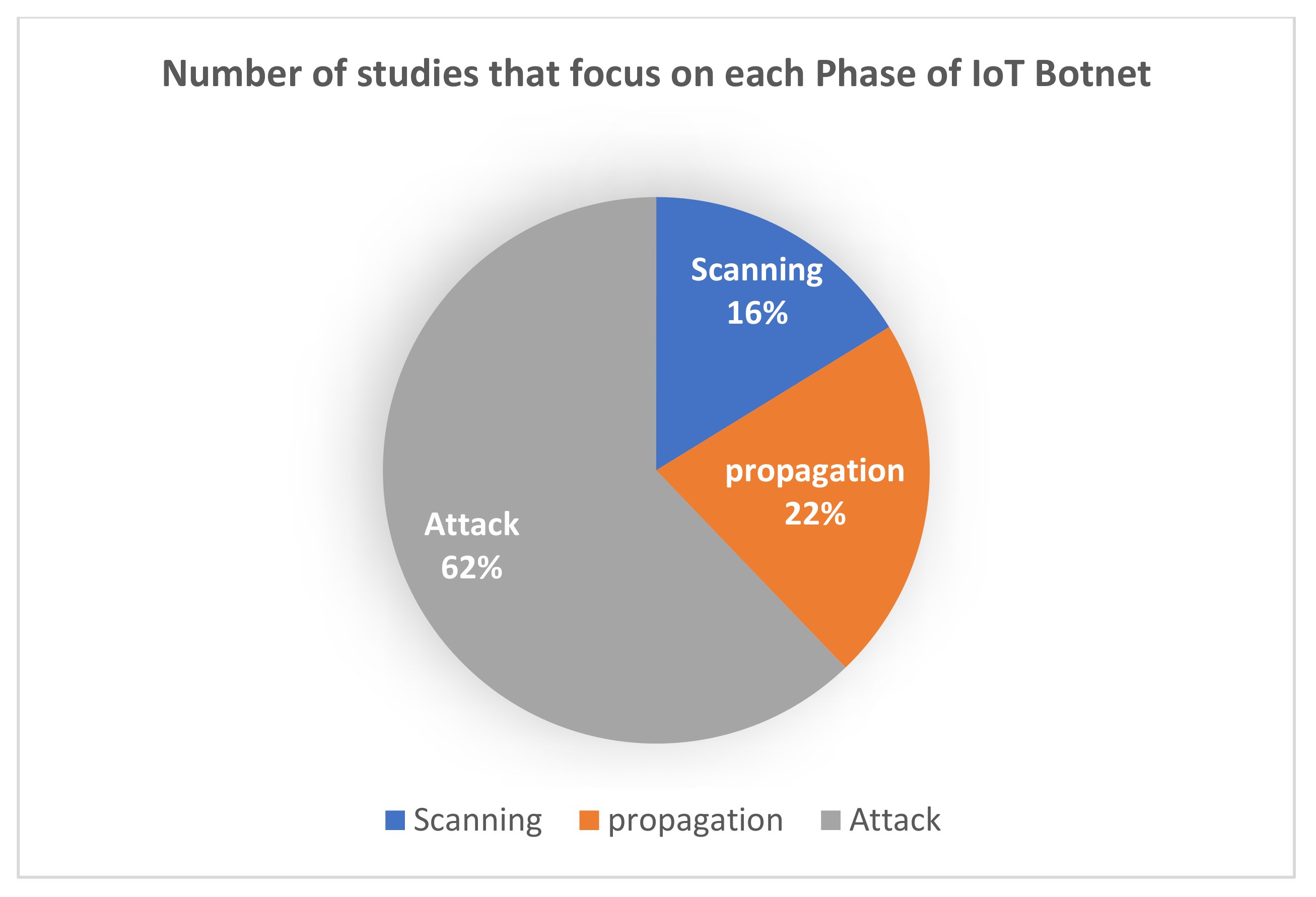
Applied Sciences | Free Full-Text | Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research | HTML

Applied Sciences | Free Full-Text | Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research | HTML
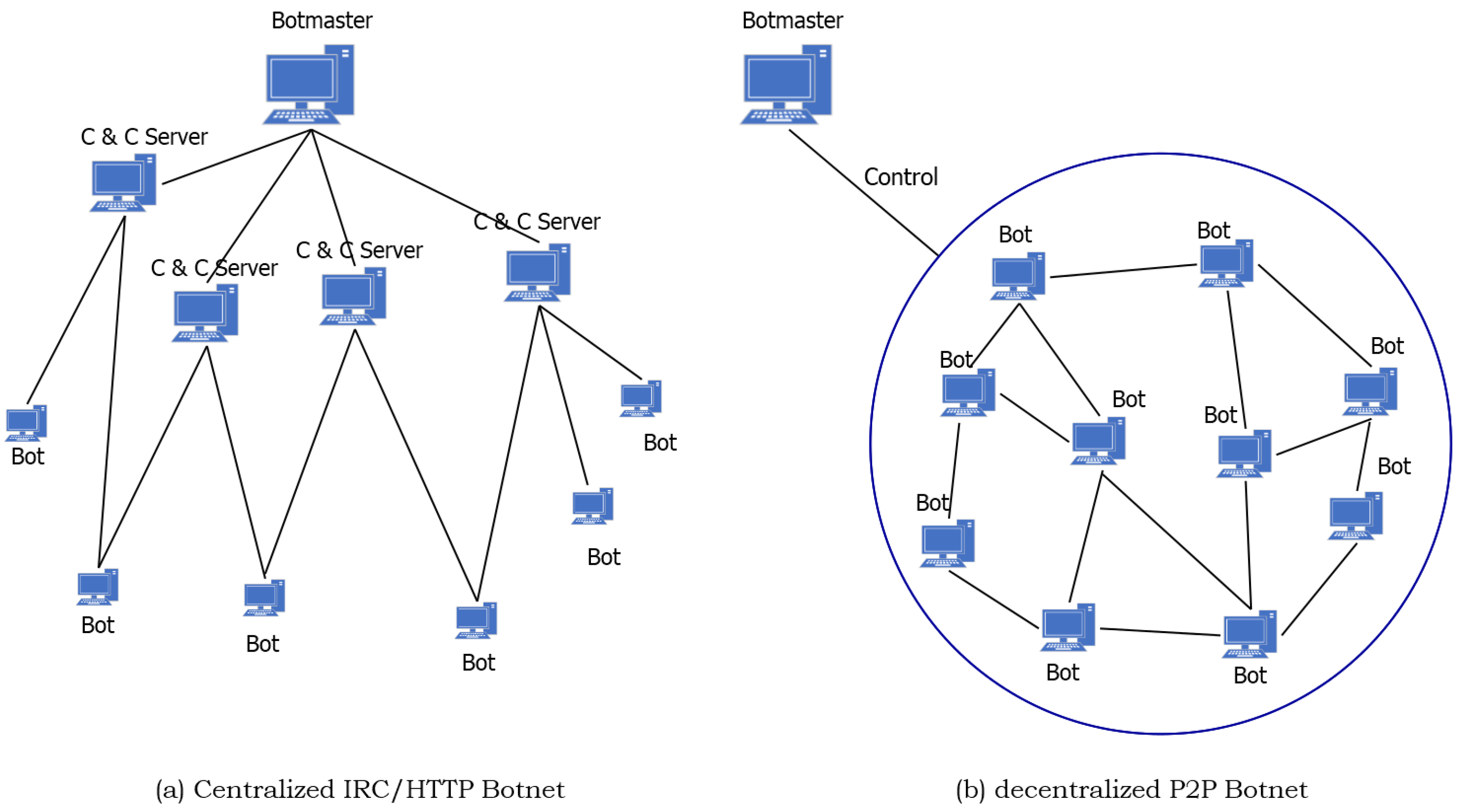
Applied Sciences | Free Full-Text | An Adaptive Multi-Layer Botnet Detection Technique Using Machine Learning Classifiers | HTML